Over the past few years, I’ve spent more time than I’d like to admit in the weeds — reviewing reports, fixing recurring bugs, writing guidance that never scales. Like many in AppSec, I’ve asked myself: Why are we still fixing the same bug classes in 2025 that we were in 2015? This frustration was the starting point for something more…
Leave a CommentMonth: July 2025
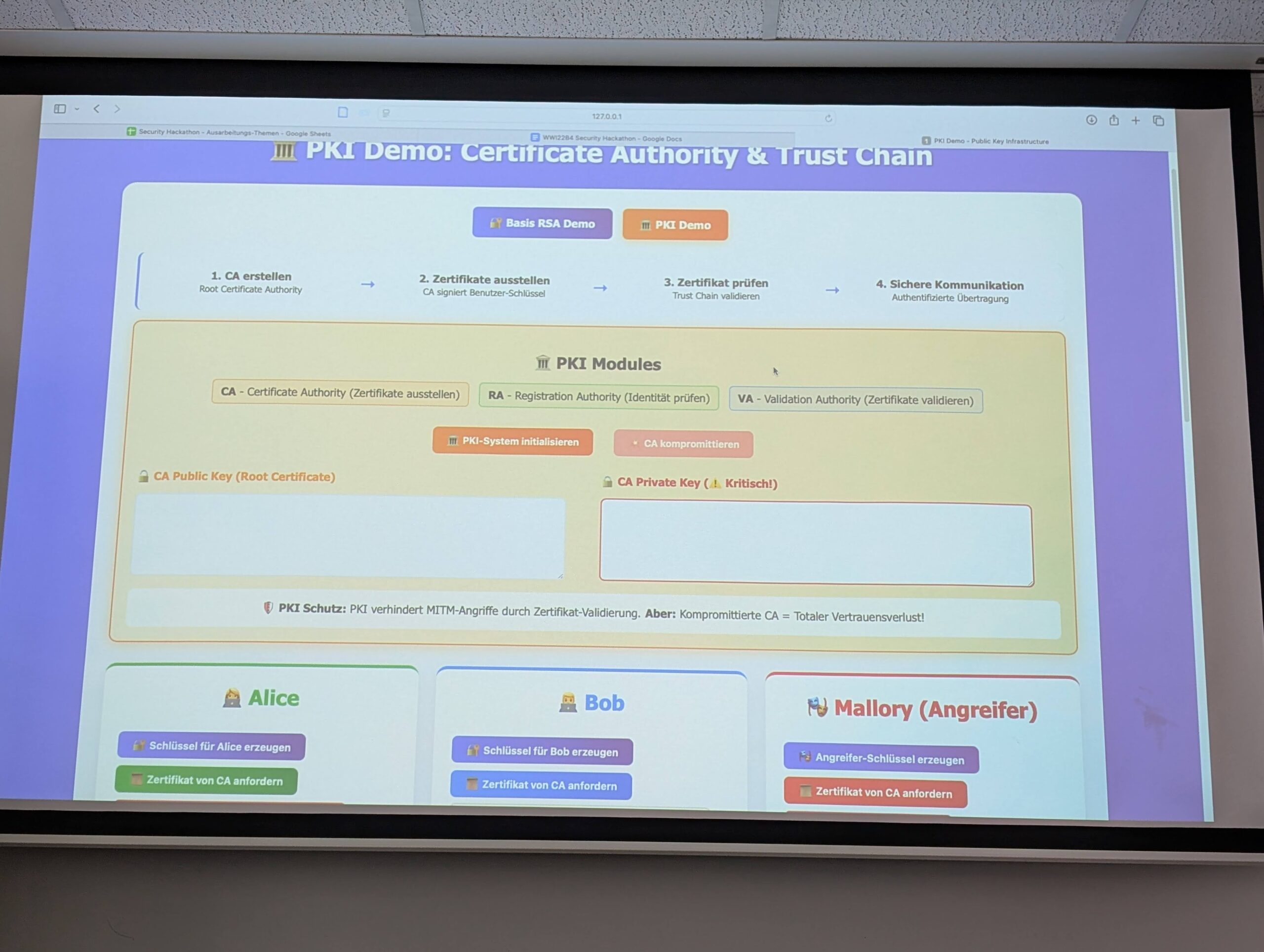
This week, the students in my Security Hackathon class at DHBW presented their final projects. The format was simple: each group selected one of the OWASP Top 10 Proactive Controls and explored it in depth. The results were more than I had hoped for. While it wasn’t required to build a working project, many groups chose to go beyond expectations,…
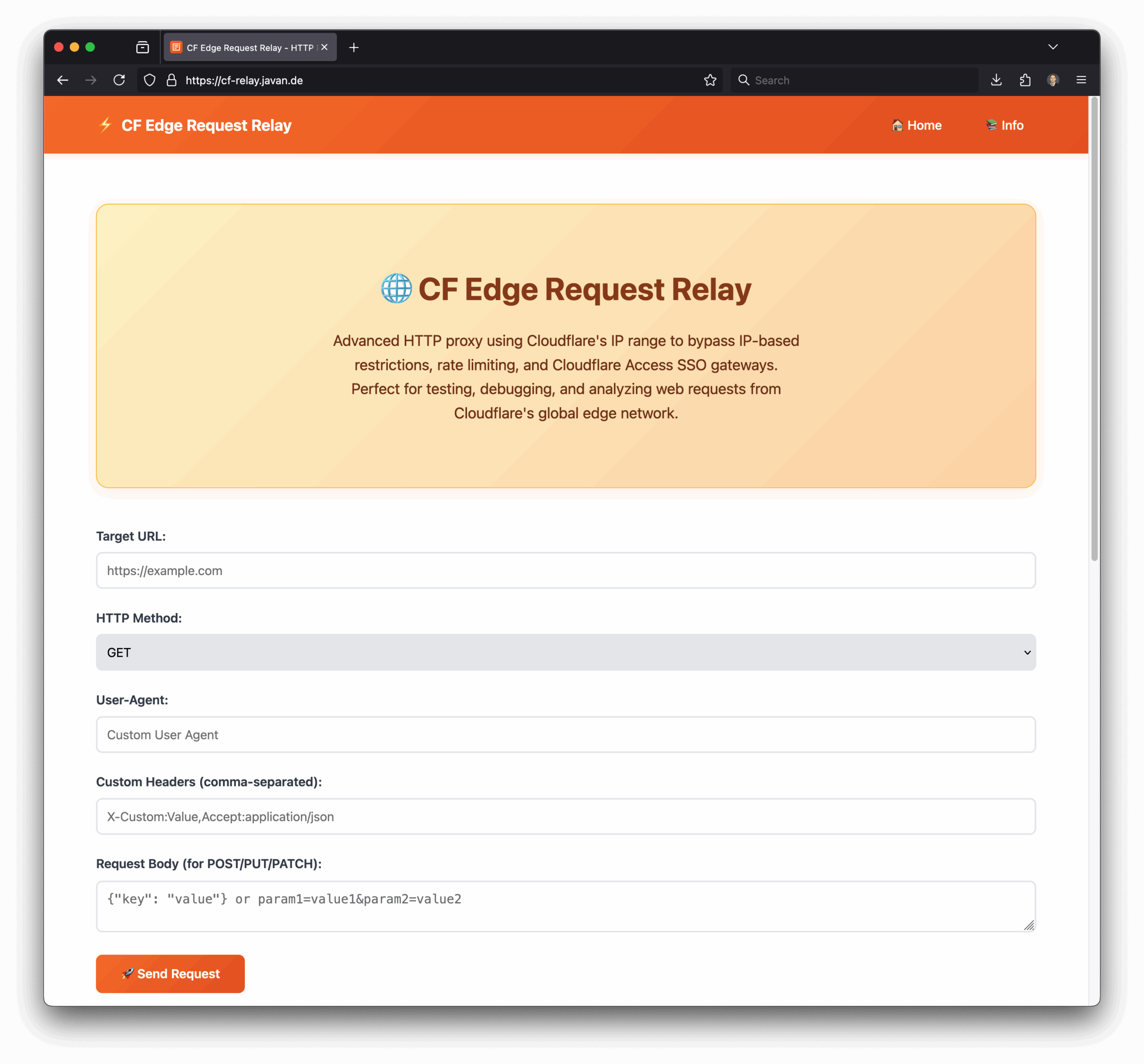
Leave a CommentThis is Part 3 of a series of multiple Cloudflare-related blog posts. Now that we have Cursor and vibe coding simple ideas into a working MVP is fun and gives you fast results, I gave it a try, one of the projects I created is: https://cf-relay.javan.de Advanced HTTP proxy using Cloudflare’s IP range to bypass IP-based restrictions, rate limiting, and…
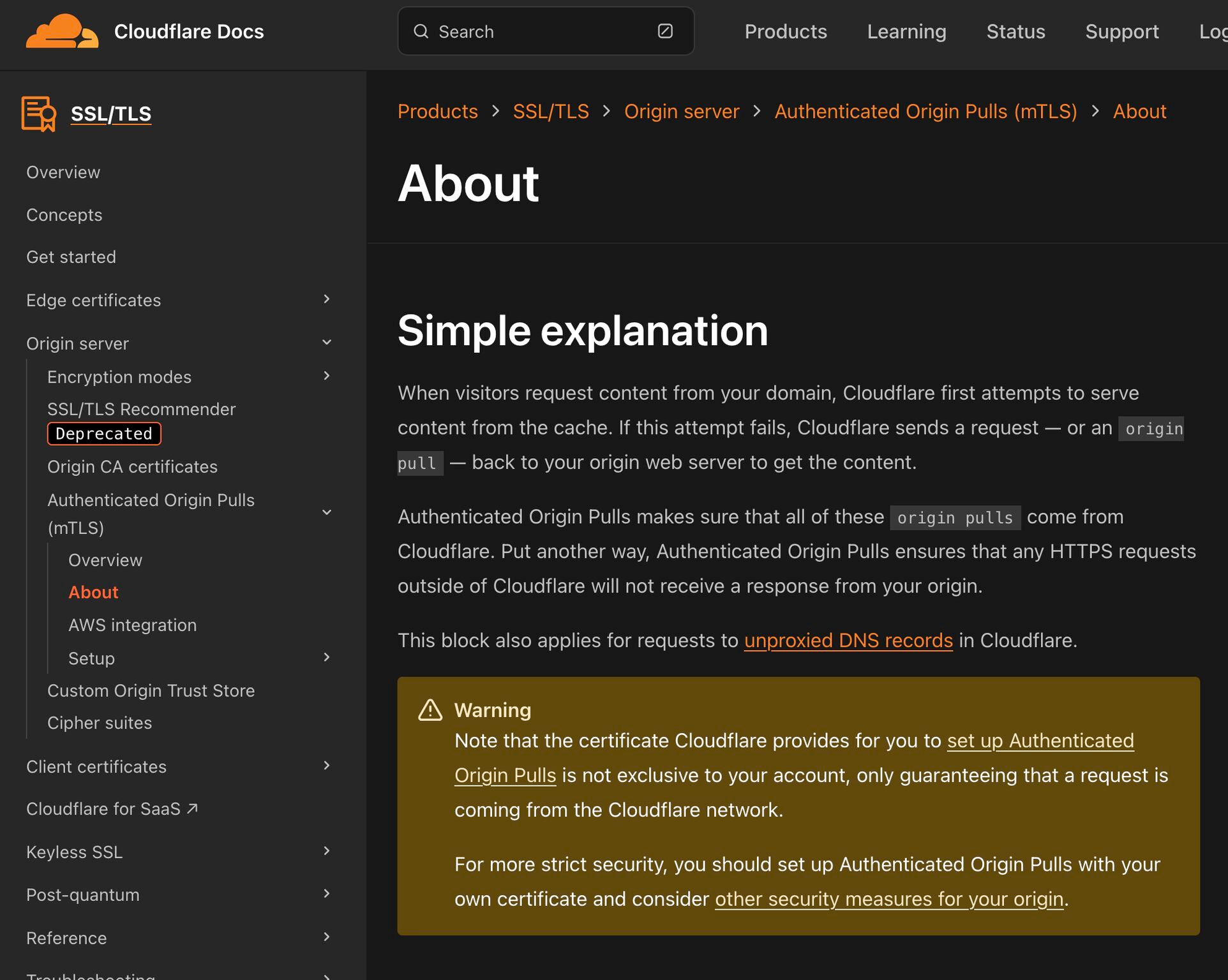
Leave a CommentFirst two search results for “blocking origin access directly” on Google showed me two misleading Cloudflare community threads, with wrong security assumption, which is why I decided to write this guide. [1] [2] The best and recommended solution is using Authenticated Origin Pulls with custom certs per domain, but as this is not trivial to set up I decided write about…
Leave a CommentEver since I installed a LEDA LUC2 fireplace, I wanted deeper insights into how it operates — particularly pressure difference, exhaust temperature, and ventilation state. Unfortunately, the vendor doesn’t provide any integration options, and the only external interface is a mysterious RJ12 port on the controller. So I decided to reverse engineer it myself. In this post, I’ll walk you…
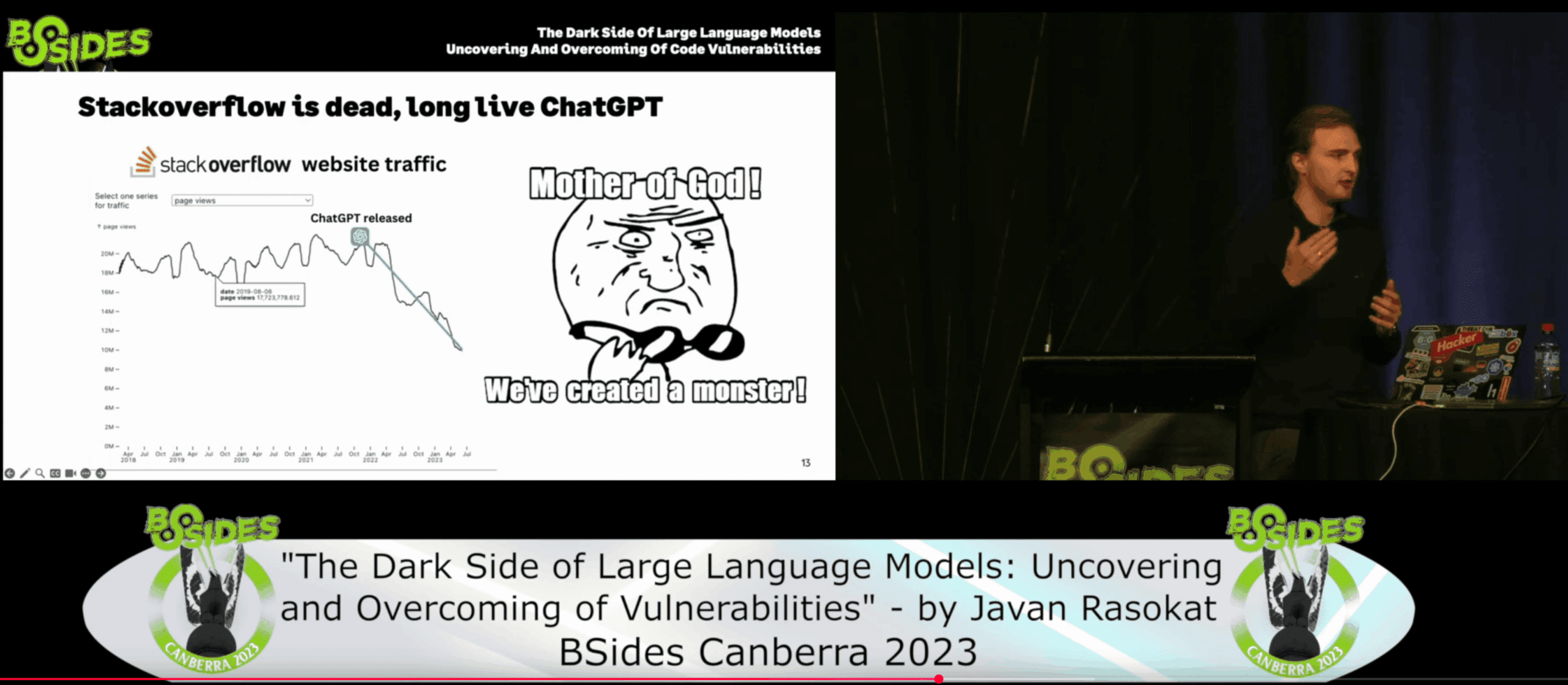
15 CommentsReflections from BSides Canberra 2023 to the Securing Sage Summit 2025 Last month at the Securing Sage Summit, I watched Sonya M. from Snyk give a slick, fast-paced live demo using GitHub Copilot. It was exactly the kind of session that draws a crowd — showing how quickly AI can help generate code from natural language prompts. But then it…
Leave a Comment