Professionally, it was a year of growth. Personally, it was one of the most intense years of my life. And none of what follows would have been possible without the support, trust, and patience of the people around me, starting at home with my wife. The biggest change came early in the year: our second child was born. Navigating work,…
Leave a CommentJavan Rasokat Posts
You know that feeling after a good conference week. You talk to smart people doing impressive work. You find one or two talks that really hit home. You fly back motivated, notebooks full, head buzzing. For the next two or three months, your energy is back. And sometimes, weeks later, one of those ideas actually turns into a real project.…
Leave a CommentI was 14 when I found my first vulnerability. It was an online game. I had no idea what responsible disclosure, bug bounty, or legal boundaries were supposed to mean. I just knew something was broken, and someone should probably know about it. So I did what made sense at the time: I joined the vendor’s IRC channel and reported…
Leave a CommentTwo weeks after DEFCON, I’m still buzzing from an unforgettable week in Vegas — one that kicked off at the Tuscany for my very first BSidesLV. And wow, what an experience. In this recap, I’ll take you through: BSidesLV has roots going back to 2009, when a bunch of talks rejected from Black Hat and DEFCON needed a home. Instead…
Leave a CommentRight now, as I’m writing this, Bitwarden is still under a mass attack. Many users (including me) are stuck in a weird deadlock state where logging into the vault is close to impossible. This made me stop and think: Luckily, I did. I found my 2FA recovery code (yep, printed on paper). But then another thought hit me: What if…
Leave a CommentOver the past few years, I’ve spent more time than I’d like to admit in the weeds — reviewing reports, fixing recurring bugs, writing guidance that never scales. Like many in AppSec, I’ve asked myself: Why are we still fixing the same bug classes in 2025 that we were in 2015? This frustration was the starting point for something more…
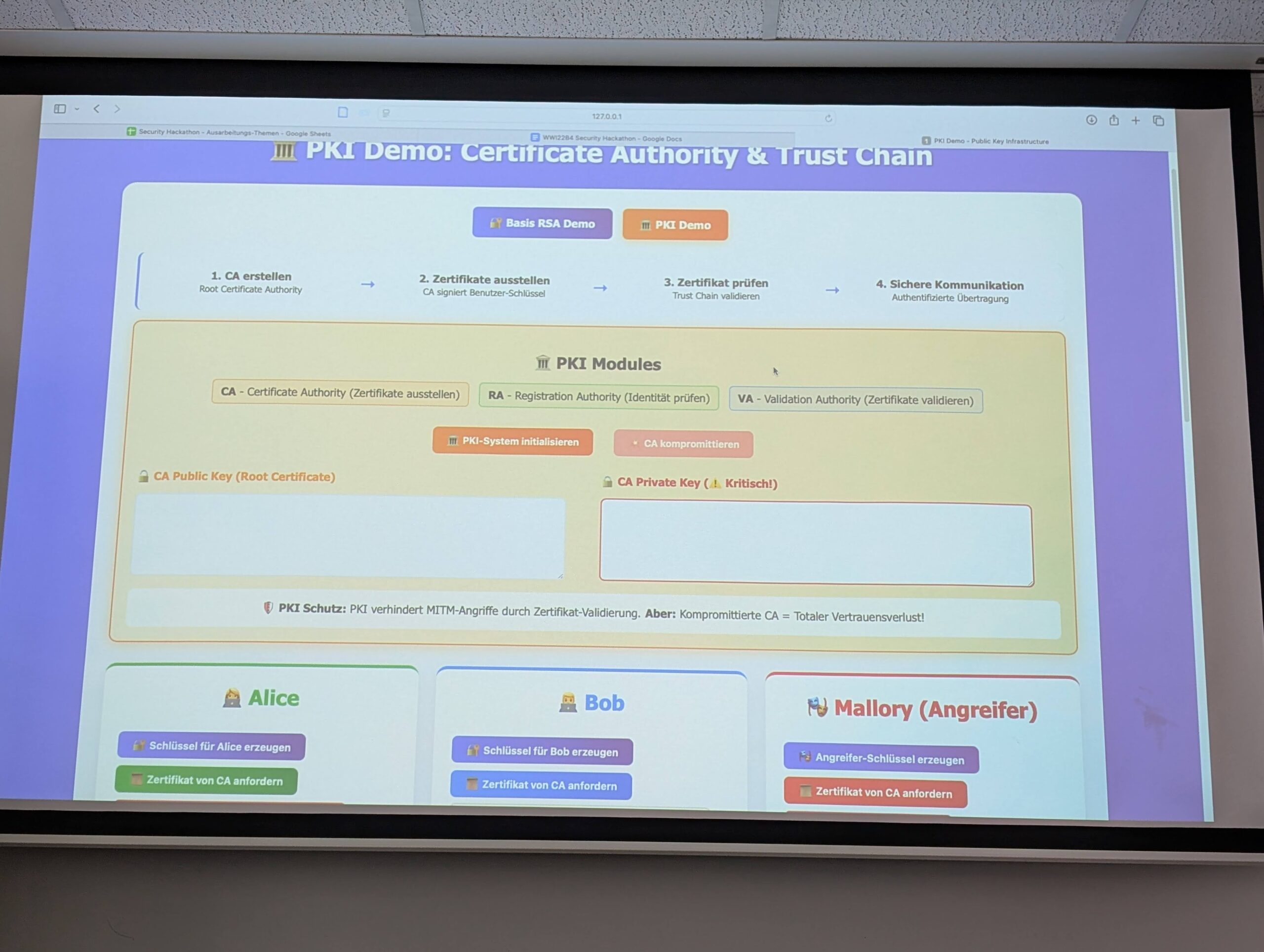
Leave a CommentThis week, the students in my Security Hackathon class at DHBW presented their final projects. The format was simple: each group selected one of the OWASP Top 10 Proactive Controls and explored it in depth. The results were more than I had hoped for. While it wasn’t required to build a working project, many groups chose to go beyond expectations,…
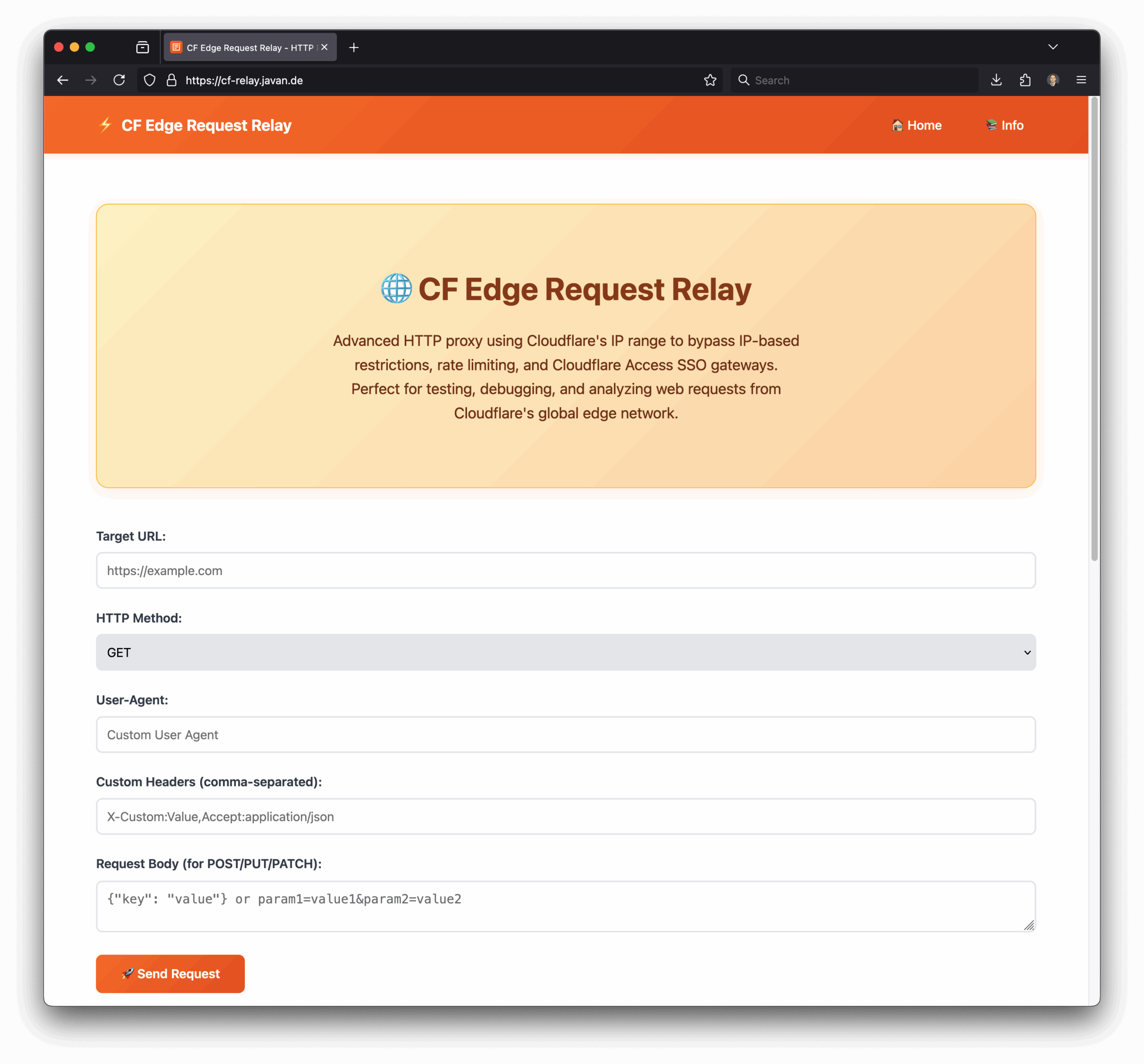
Leave a CommentThis is Part 3 of a series of multiple Cloudflare-related blog posts. Now that we have Cursor and vibe coding simple ideas into a working MVP is fun and gives you fast results, I gave it a try, one of the projects I created is: https://cf-relay.javan.de Advanced HTTP proxy using Cloudflare’s IP range to bypass IP-based restrictions, rate limiting, and…
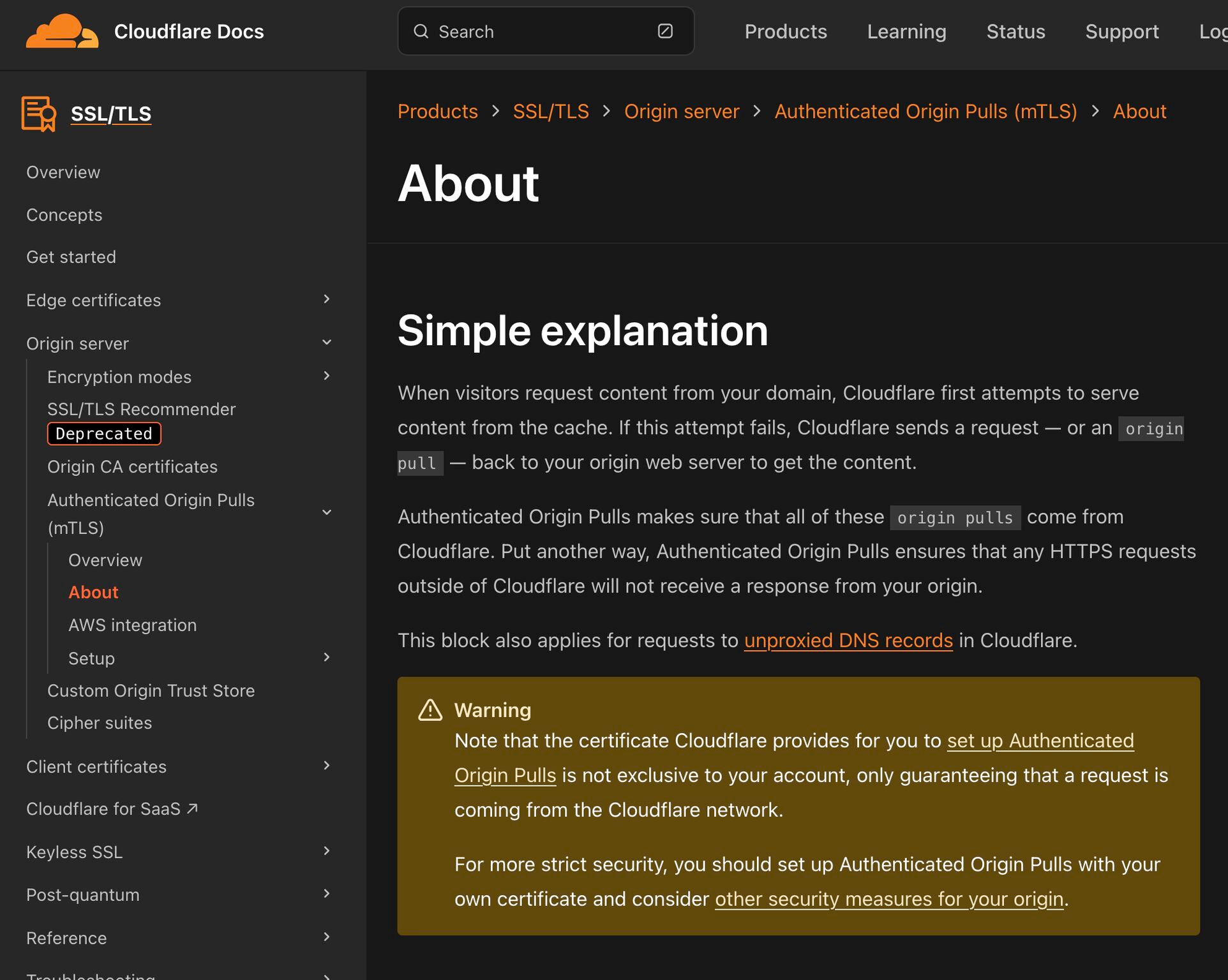
Leave a CommentFirst two search results for “blocking origin access directly” on Google showed me two misleading Cloudflare community threads, with wrong security assumption, which is why I decided to write this guide. [1] [2] The best and recommended solution is using Authenticated Origin Pulls with custom certs per domain, but as this is not trivial to set up I decided write about…
Leave a CommentEver since I installed a LEDA LUC2 fireplace, I wanted deeper insights into how it operates — particularly pressure difference, exhaust temperature, and ventilation state. Unfortunately, the vendor doesn’t provide any integration options, and the only external interface is a mysterious RJ12 port on the controller. So I decided to reverse engineer it myself. In this post, I’ll walk you…
15 Comments