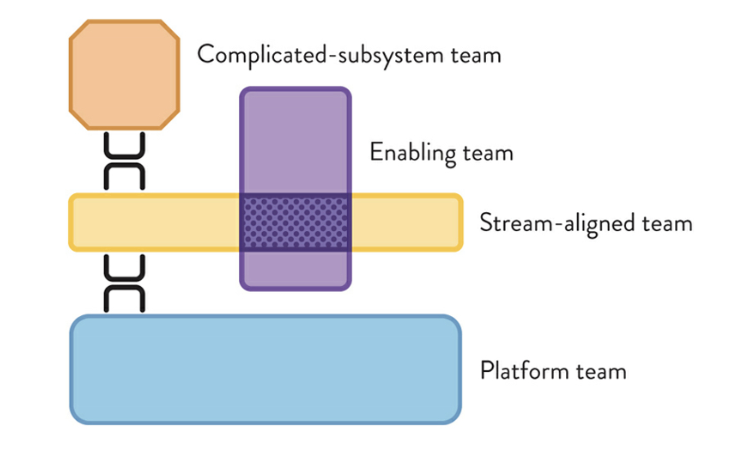
In a world where security needs to move as fast as software delivery, how we structure our AppSec (Application Security) teams is more critical than ever. The right team topology can make the difference between a well-secured application and a bottlenecked security process. Before looking in detail into these structures, let’s break down some essential team types that shape how…
Leave a CommentJavan Rasokat Posts
Over the past few years, the concept of “shift-left” has dominated software security. The idea seems intuitive – catch vulnerabilities as early as possible in the development process, allowing teams to remediate issues long before they ever reach production. But after a recent discussions, I started thinking more critically about what shift-left actually delivers and, more importantly, where it might…
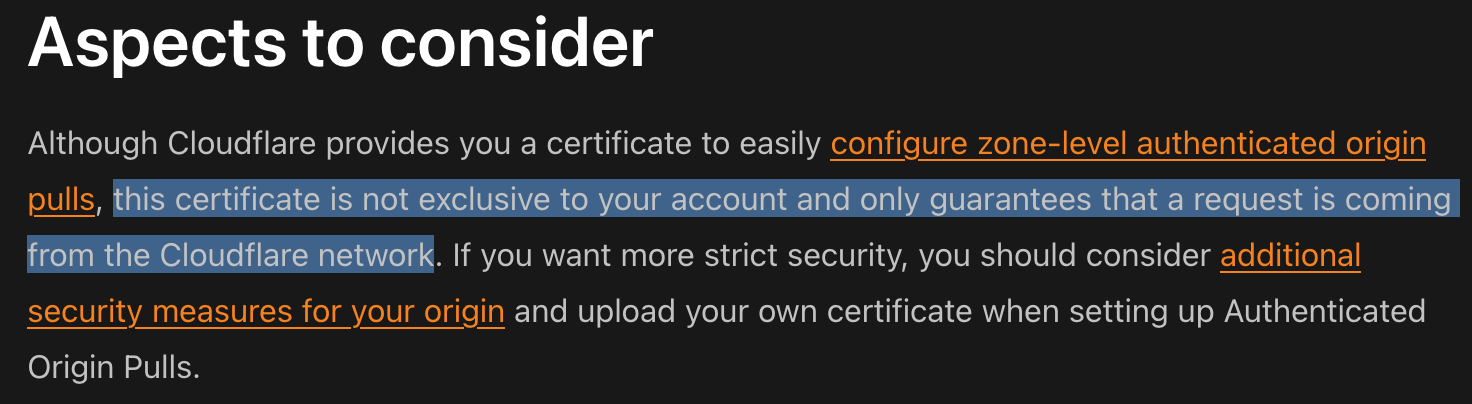
Leave a CommentThe Misconception IP allowlisting involves configuring your origin server to accept connections only from specific IP addresses – in this case, Cloudflare’s IP ranges. The logic seems sound: by allowing only trusted IPs, you reduce the risk of unauthorized access. Unfortunately, this method overlooks several attack cases that can be exploited. My Observation Over the years, I’ve noticed numerous security…
Leave a CommentWordPress is the most widely used CMS of all. But after the setting it up, most do not think further about security. Therefore, vulnerabilities in WordPress are particularly lucrative. Outdated versions, for which public vulnerabilities are known, are detected and attacked by so-called crawlers and bots. This usually happens fully automatically. Often the goal of these automated attacks is to…
Leave a CommentI had a great time last week at OWASP Frankfurt’s 63rd meetup all about #GenerativeAI and #Security! We dived into deep fake detection and ways to bypass it – truly eye-opening.We also explored the impact of AI generated code on software security with a GitHub Copilot case study. Plus, plenty of pizza and some fantastic home-brewed beer by Check24. If…
Leave a CommentDuring my time in Toronto, it was not just about security of LLMs but also a lot about reunion and meeting fantastic people, one story I definitely wanted to share with you: Four years ago, in my previous role at EXXETA in Stuttgart I was mentoring Fabian, an enthusiastic working student. Since then, it’s almost as if fate keeps bringing…
Leave a CommentJust wrapped up my second session on Software Quality Engineering co-lecturing with Prof. Dr. Katja Wengler at DHBW Center for Advanced Studies in Heilbronn, Germany, and I’m once again struck by the incredible dynamism of these lectures. The level of engagement always astounds me. 👉 Day 1 was all about DevSecOps and Secure-SDLC, where we dived into secure coding practices,…
Leave a CommentI had a great time speaking at ThreatCon.io Hacking Conference in beautiful Kathmandu, Nepal. During my talk we discussed the new world of LLM auto-suggested code and therefore it’s influence on secure coding. One of the key findings I demoed is, that while tools like GitHub Copilot can speed things up, they sneak in various vulnerabilities. But we also discussed…
Leave a CommentThese vulnerabilities have a common characteristic: they are inherent features of programming languages or libraries. However, it took a considerable amount of time for them to be recognized as attack vectors and actual vulnerabilities. The existence of these vulnerabilities, previously unknown until their public disclosure, resulted in a substantial and previously unidentified attack surface for malicious actors. This discovery had…
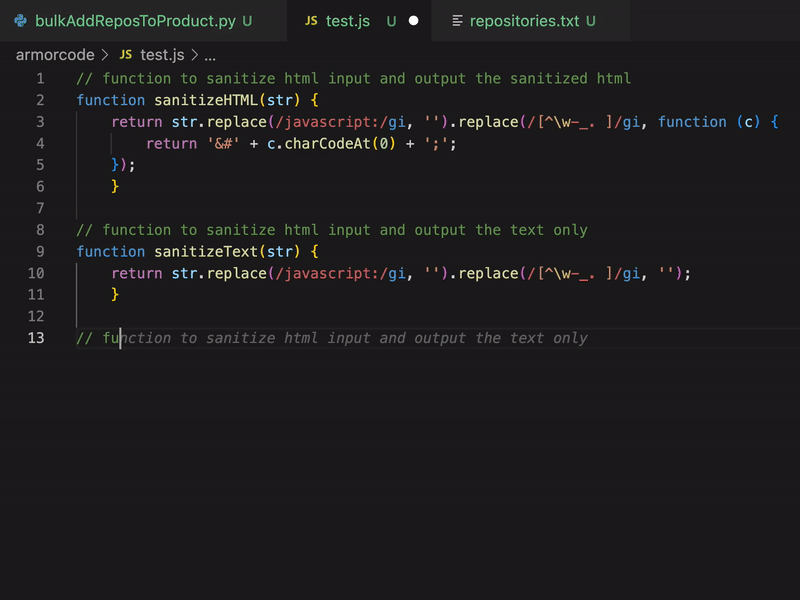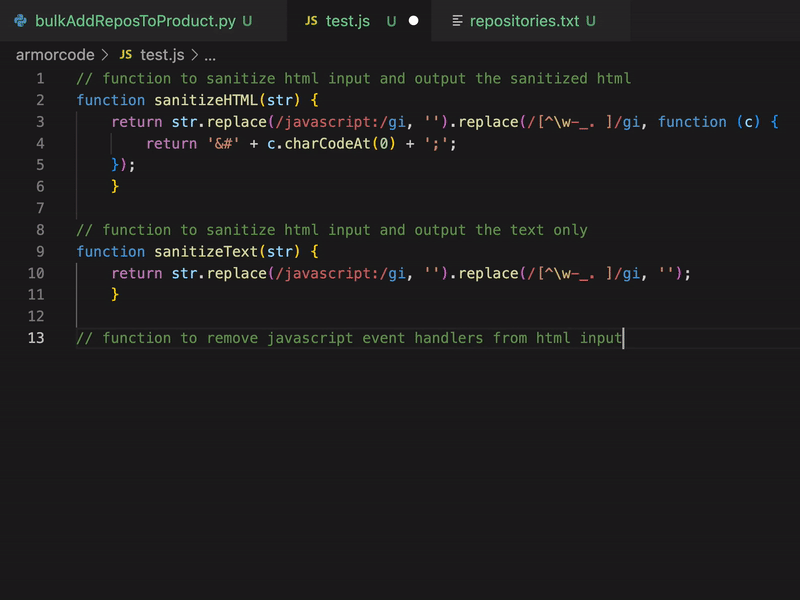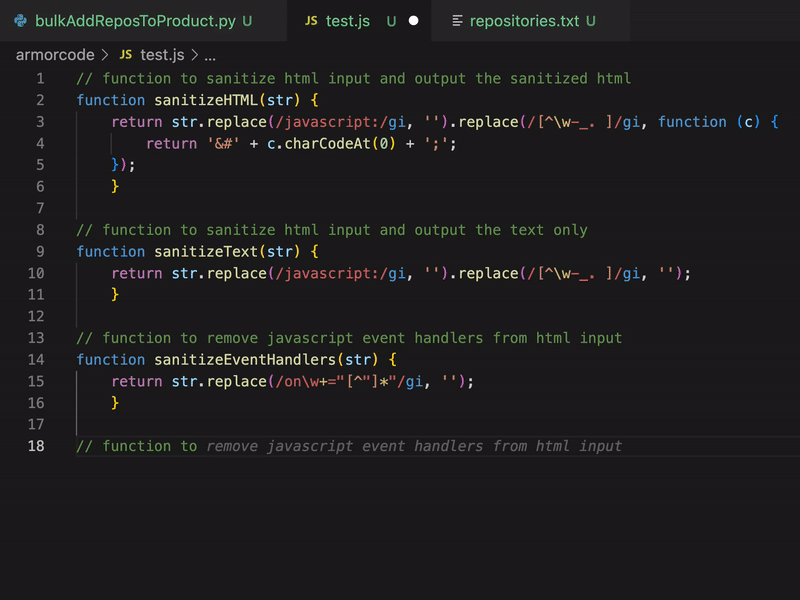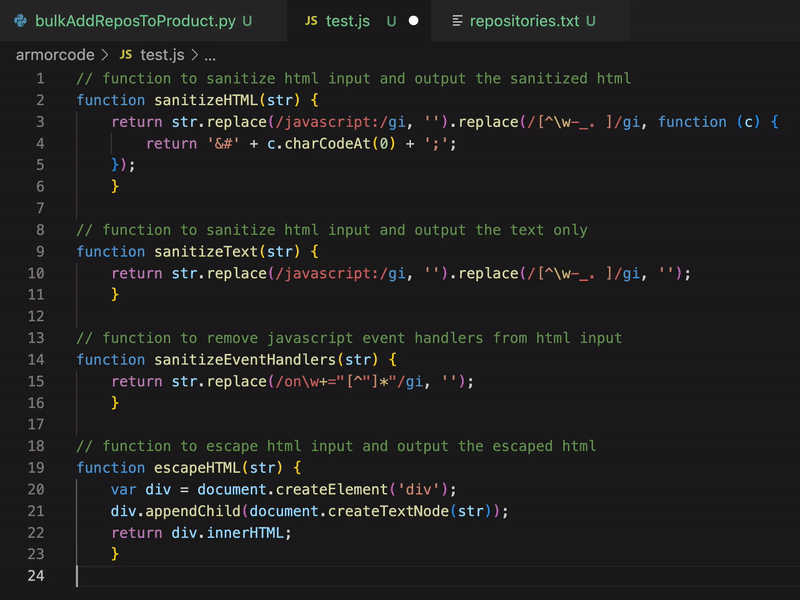
Leave a CommentToday I developed a python tool to automate some processes in our vulnerability management. For this task I decided to use GitHub Copilot. Mostly by using code comments (#, //) Copilot wrote the code for me, so I did not have to care much about syntax or function names, which I keep forgetting when I am not coding in Python…
Leave a Comment