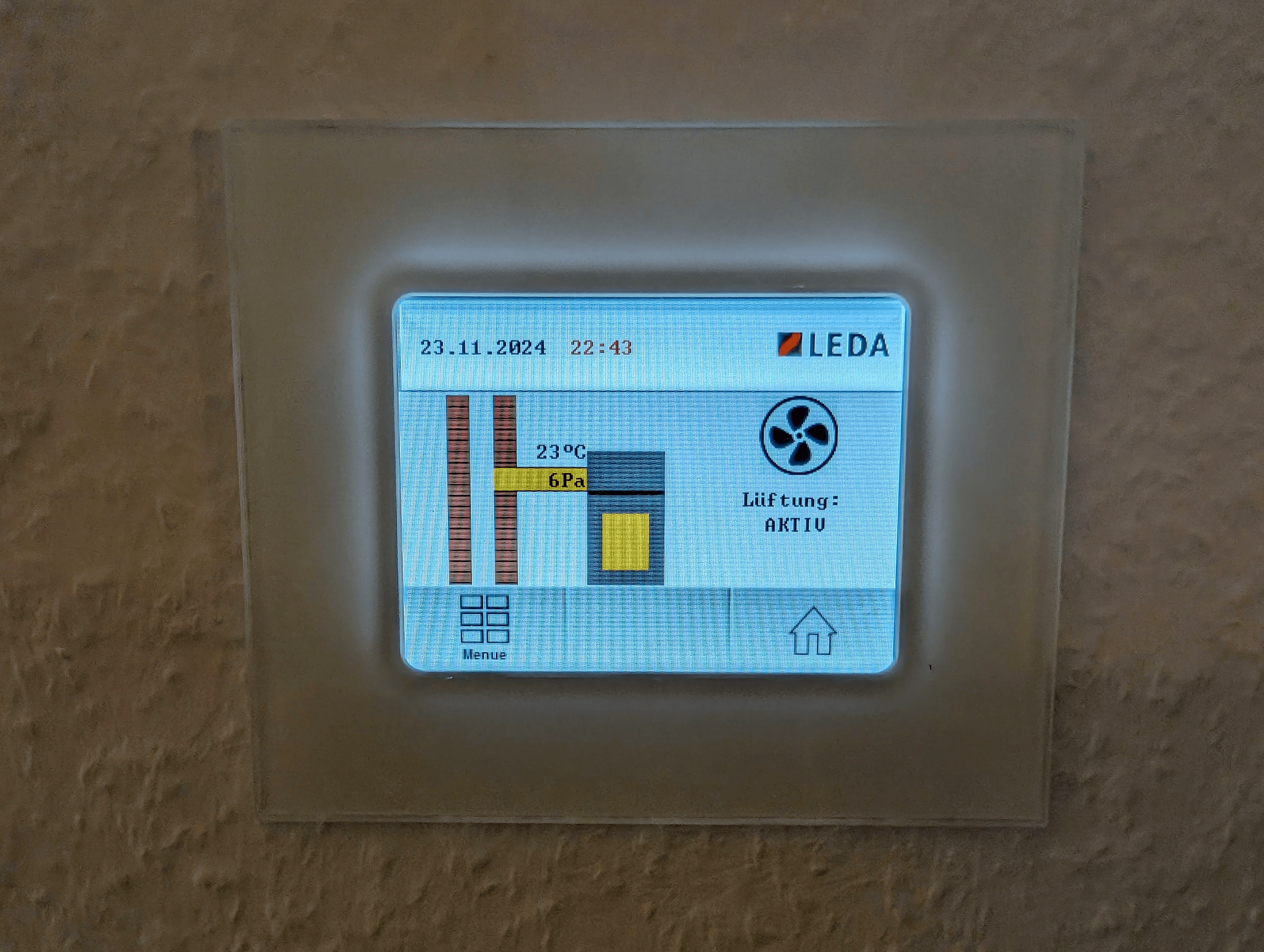
Ever since I installed a LEDA LUC2 fireplace, I wanted deeper insights into how it operates — particularly pressure difference, exhaust temperature, and ventilation state. Unfortunately, the vendor doesn’t provide any integration options, and the only external interface is a mysterious RJ12 port on the controller.
So I decided to reverse engineer it myself.
In this post, I’ll walk you through how I decoded the CAN bus communication of the LEDA LUC2, used an ESP32 with an MCP2515 module to read the values, and made them available in Home Assistant using ESPHome. Even better: the method works for any CAN-based system.
Step 1 – Sniffing the CAN Bus
I started by simply listening to the bus without sending anything. The goal was to see what kind of messages the LUC2 sends when it’s running.
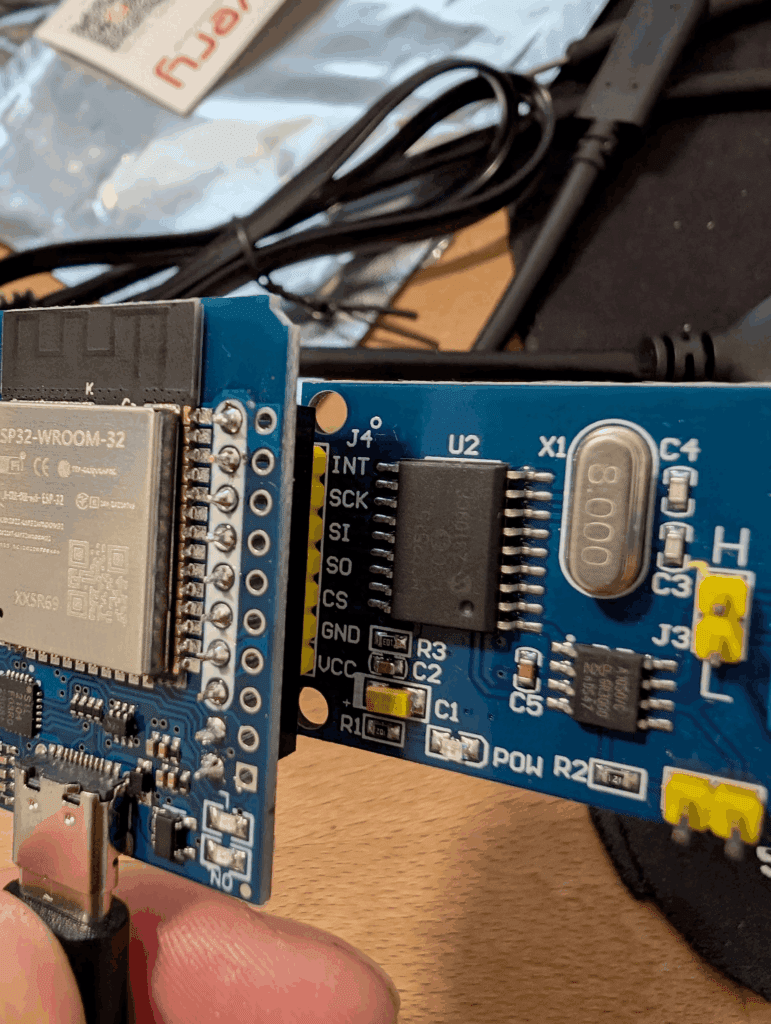
The RJ12 port on the controller exposes a CAN High / CAN Low line, so I used an MCP2515 CAN transceiver paired with an ESP32 to tap into it passively.
Required Hardware
- ESP32 Dev Board
- MCP2515 CAN module (with TJA1050 transceiver)
- RJ12 breakout or RJ12 splitter (so the main unit can keep working)
- USB-C buck converter (12 V → 5 V to power ESP32 from the fireplace)
- A few jumper wires
Step 2 – Wiring it Up
Here’s how I wired the ESP32 to the MCP2515 over SPI:
| MCP2515 Pin | ESP32 Pin |
|---|---|
| VCC | 3.3V |
| GND | GND |
| CS | GPIO16 |
| SCK | GPIO22 |
| MOSI | GPIO21 |
| MISO | GPIO17 |
| INT | Not used |
Then, I connected the CAN_H and CAN_L from the MCP2515 to the RJ12 port using a breakout cable. On the LEDA LUC2, the pinout of the RJ12 is:
| RJ12 Pin | Signal |
|---|---|
| Pin 1 | 12V (used to power the ESP32 via buck converter) |
| Pin 2 | unused |
| Pin 3 | unused |
| Pin 4 | CAN-L |
| Pin 5 | CAN-H |
| Pin 6 | GND |
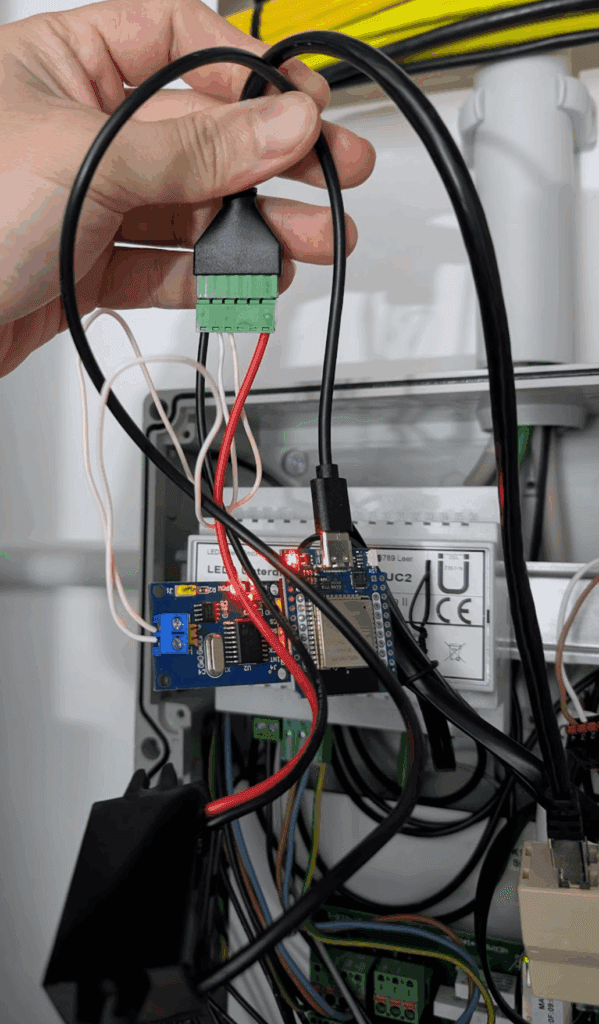
⚠️ Note: Several users (including me, in early tests) accidentally swapped CAN-H and CAN-L, which results in no data being received. Make sure to get the polarity right.
Step 3 – Logging Raw CAN Frames
Once everything was connected, I flashed this minimal ESPHome YAML just to see what the fireplace was sending:
spi:
clk_pin: GPIO22
miso_pin: GPIO17
mosi_pin: GPIO21
canbus:
- platform: mcp2515
cs_pin: GPIO16
bit_rate: 125KBPS
on_frame:
- can_id: 0x28A
then:
- logger.log:
format: "Raw frame: %s"
args: [x]
I immediately started seeing messages on CAN ID 0x28A as the device is constantly measuring temperature and sending those values to it’s display. From here, I started dumping frames and inspecting the payloads over time.
Step 4 – Decoding the Messages
After collecting enough frames, I started to spot patterns:
- Messages always 8 bytes
- Byte 0 = message type
- Message Type 0x00 = sensor values
- Message Type 0x01 = status info
Example frame (Type 0x00):
00 03 E1 32 00 00 00 00- Byte 0: 00 → Type 0
- Byte 1: 03 → Pressure value
- Byte 2: E1 → Modifier / condition byte
- Byte 3: 32 → Temperature (in °C)
I decoded pressure using this logic:
float pressure = x[1] * 0.1f;
if (x[2] == 0x81) {
pressure += 25.5f;
}The result? Actual pressure difference values like 26.5 Pa or 29.1 Pa. Same with exhaust temperature — a direct value in °C from Byte 3.
Step 5 – Integrating Into Home Assistant
I extended the ESPHome config to publish proper sensors:
sensor:
- platform: template
name: "Pressure Difference"
id: pressure_difference_sensor
unit_of_measurement: "Pa"
- platform: template
name: "Exhaust Temperature"
id: exhaust_temperature_sensor
unit_of_measurement: "°C"
binary_sensor:
- platform: template
name: "Ventilation Active"
id: ventilation_status_sensorAnd the full on_frame decoding logic:
on_frame:
- can_id: 0x28A
then:
- lambda: |-
if (x.size() == 8) {
uint8_t type = x[0];
if (type == 0x00) {
float pressure = x[1]*0.1f + (x[2]==0x81 ? 25.5f : 0);
float temp = x[3];
id(pressure_difference_sensor).publish_state(pressure);
id(exhaust_temperature_sensor).publish_state(temp);
} else if (type == 0x01) {
bool vent = (x[5] == 0x01);
id(ventilation_status_sensor).publish_state(vent);
}
}As soon as ESPHome connects to Home Assistant, you’ll see these as regular sensors — ready for dashboards or automations.
Step 6 – Automation Ideas
Here are a few things I did once the data was available in Home Assistant:
- Low exhaust temperature alert: Push notification when fire needs reloading
- Auto-ventilation: Trigger fans based on pressure + ventilation status
- Trends: Long-term statistics and graphs of fireplace performance
Step 7 – Applying This to Other CAN Devices
This process works for any CAN device — not just LEDA:
- Sniff traffic using ESPHome and log raw frames
- Decode byte structure manually (you’ll get better with practice)
- Create sensors for useful values
Whether you’re working on solar inverters, EV chargers, or even cars, the approach is the same.
How Can You Discover Relevant CAN IDs on Other Devices
When applying this to other CAN systems, here’s a step-by-step process:
1. Log All CAN Traffic
Start with a generic logger in ESPHome or Arduino:
on_frame:
- then:
- logger.log:
format: "ID: 0x%03X -> %s"
args: [id, x]Let it run for a few minutes and save the output.
2. Identify Repeating IDs
Look for:
- Periodic messages (same ID every second)
- Changing payloads (values that vary with time, temperature, input, etc.)
- Matching value changes to real-world actions
- Decoding payload bytes manually
- Iterating and testing
Final Thoughts
Reverse-engineering the LEDA LUC2 turned into a fun little weekend project — and now I have full visibility into my fireplace from anywhere. No cloud, no vendor lock-in, no guessing when to reload wood.
Everything I used is published here:
🧠 ESPHome config: 👉 https://gist.github.com/JavanXD/696d026ef202a7d6455ed4745df63e39
Enjoy the fire. 🔥

Nice work on reading the CAN Bus Data from the fireplace. I’d like to do something similar for a steam shower generator that has RJ12 ports. How did you determine that the communication protocol was a CAN bus?
Good point – in my case I actually knew it upfront from the manufacturer documentation.
great project, thanks for sharing your work.👍
Being my first ESP32 project, I learned a lot. I had to change the pin configuration for my setup which I don’t understand for the the time being… I’m going the use the pressure difference also to monitor the condition of the filter medias belonging to our ventilation system.
Love that use case,
I used the pressure difference to detect wind busts outside. It clearly shows wind busts.
Hi,
cool project, I have the same controller and want to implement it the same way. But I am not sure about the power supply. Is the 12V coming via the rj12 enough to power the esp? Because it also supplies the LUC display controller. I cannot find a specification on the power if the 12V output of the rj12 port from the LUC controller.
BR
Sebastian
Yes, I used the pin 1 and 6 from the RJ12 for the 12V.
Hi, i have used same hardware for my Schmid SMR Control. I had to put the MCP board to 3,3V, instead of 5V and swapped H/L. Frames on can_id 280 and 28B. Temperature values, PWM of pump and air throttle was found.
But after 4 hours the frames stopped. Any idea?
Congrats on your set up – nice!
As a workaround you can add a restart button to your ESPHome:
button:- platform: restart
name: "CAN-Sniffer Restart"
And have a automation triggering this button if there is no data received.
But I do not have that issue, so I don’t need it.
Hey Javan,
cool project.
I have a question about the “Pressure Difference”: it always returns a positive value, regardless of whether the air pressure is negative.
Is there a way to change that? That would be quite important for me.
Thanks!
If we know the bytes that represent the negative value we can fix it.
Unfortunately I never had negative pressure so I can’t test it.
I see.
So currently I have almost every day negative pressure values.
Would it help, when I proceed with “Step 3 – Logging Raw CAN Frames” and share the logs?
Thanks,
Stefan
Hi Stefan,
if you change the code to the following it could work:
// Extract pressure difference from Byte 2 (x[1])(x[1]); // signed 8-bit int8_t raw_pressure = static_cast
float pressure_difference = raw_pressure * 0.1f; // scale to Pa
The current pressure measurement code can never produce a negative number, because x[1] is in the range 0..255. So if the device sends negative pressure using a signed encoding (most commonly two’s complement in an 8-bit field), values that should be negative arrive as 128..255 and you display them as positive.
The new code block is trying to fix this.
Hi everyone!
Very cool project and special thanks for posting the individual steps. That was very helpful!
Can anyone please upload the communication protocols between LEDA components, ispecially master to slave?
I have a LEDA KS04 (circulation pump for water included fire place). I do not ave any other device, so there is no ongoing communication I can listen to, and the device itself does obviously not talk without trigger from a Master device. Any ideas?
Hello
unfortunately my comment was deleted somehow. Anyway, i´ll try it again.
I have the problem, that I only have a slave device. Its a KS04, the circulation pump of a fire place with water heat exchanger.
There is no Master the device speaks to, but it is possible to buy other devices like controller or sth.
I have the feeling, that the KS04 only sends data if there is a request. But I do not know hoe this request should look like. Any ideas how to find out? Can you maybe show screenshots of the protocol your master uses to talk to your slave?
Thanks in advance!
Hi Javan,
thanks for the code.
I just compiling and testing it 🙂
I’ll update, when I’ll get a negative pressure 😉
Thanks,
Stefan