This is Part 3 of a series of multiple Cloudflare-related blog posts.
- Part 1: https://javan.de/relying-solely-on-ip-allowlisting-with-cloudflare-is-wrong/
- Part 2: https://javan.de/how-to-prevent-cloudflare-proxy-bypasses/
Now that we have Cursor and vibe coding simple ideas into a working MVP is fun and gives you fast results, I gave it a try, one of the projects I created is:
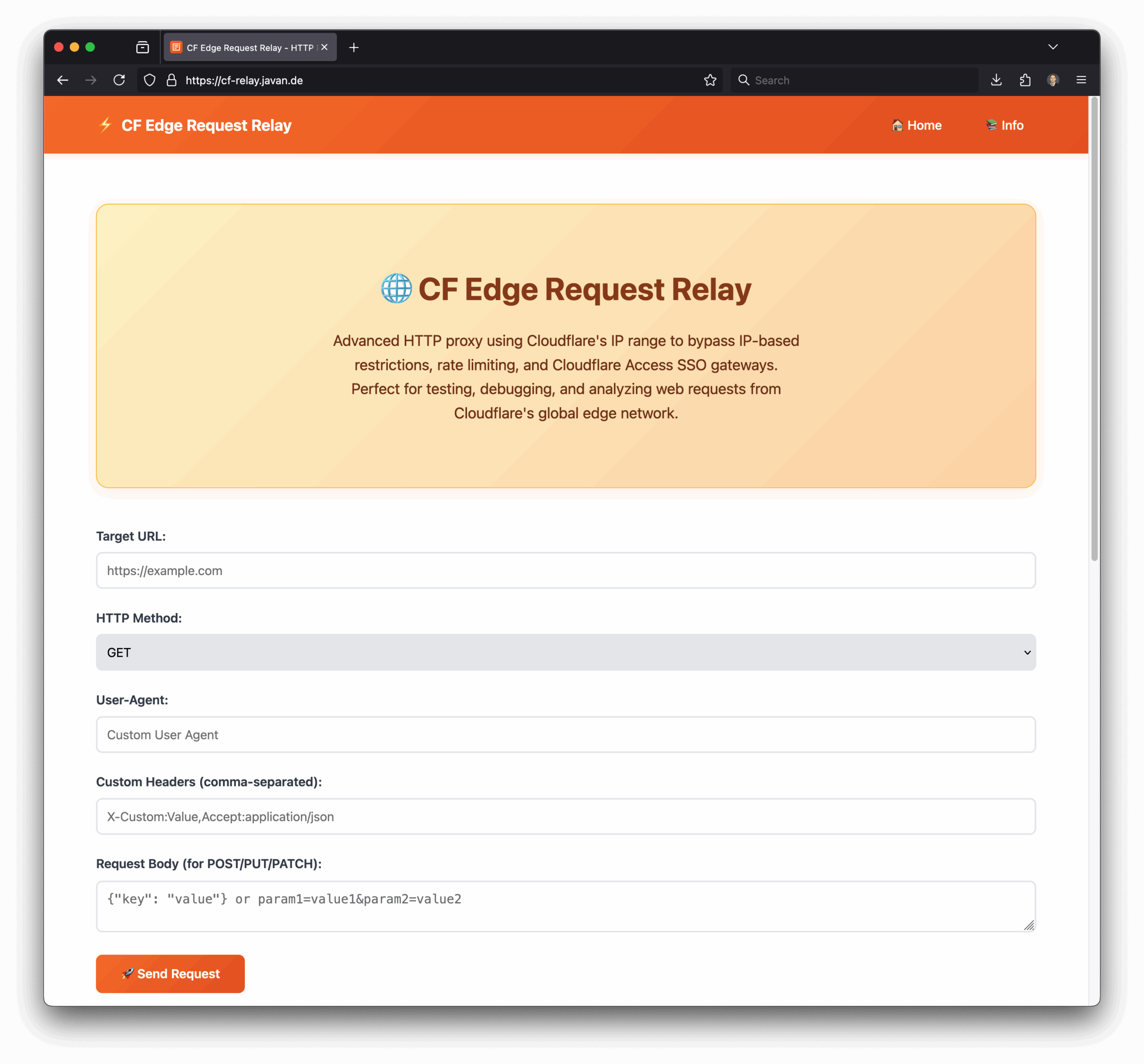
https://cf-relay.javan.de
Advanced HTTP proxy using Cloudflare's IP range to bypass IP-based restrictions, rate limiting, and Cloudflare Access SSO gateways. Perfect for testing, debugging, and analyzing web requests from Cloudflare's global edge network.
For example if you access with your browser
it shows you your IP address, but if you access it with the HTTP proxy
it shows a IP from Cloudflare. You can cross-check with this list.
Cloudflare’s Threat Model
It must have been part of Cloudflare threat model, because there are known and documented limitations.
1) Requests to IP addresses are blocked by Cloudflare.
2) resolveOverride – this option was disabled in Cloudflares Workers implementation of node-fetch.
Directs the request to an alternate origin server by overriding the DNS lookup. The value of resolveOverride specifies an alternate hostname which will be used when determining the origin IP address, instead of using the hostname specified in the URL. The Host header of the request will still match what is in the URL. Thus, resolveOverride allows a request to be sent to a different server than the URL / Host header specifies. However, resolveOverride will only take effect if both the URL host and the host specified by resolveOverride are within your zone. If either specifies a host from a different zone / domain, then the option will be ignored for security reasons. If you need to direct a request to a host outside your zone (while keeping the Host header pointing within your zone), first create a CNAME record within your zone pointing to the outside host, and then set resolveOverride to point at the CNAME record. Note that, for security reasons, it is not possible to set the Host header to specify a host outside of your zone unless the request is actually being sent to that host.
3) Setting a custom “Host” header will be ignored by node-fetch. This had not always been the case but was directly patched in node-fetch itself before. (see here: https://github.com/nodejs/node/issues/50305 )