Just wrapped up my second session on Software Quality Engineering co-lecturing with Prof. Dr. Katja Wengler at DHBW Center for Advanced Studies in Heilbronn, Germany, and I’m once again struck by the incredible dynamism of these lectures. The level of engagement always astounds me. 👉 Day 1 was all about DevSecOps and Secure-SDLC, where we dived into secure coding practices,…
Leave a CommentCategory: AppSec
I had a great time speaking at ThreatCon.io Hacking Conference in beautiful Kathmandu, Nepal. During my talk we discussed the new world of LLM auto-suggested code and therefore it’s influence on secure coding. One of the key findings I demoed is, that while tools like GitHub Copilot can speed things up, they sneak in various vulnerabilities. But we also discussed…
Leave a CommentThese vulnerabilities have a common characteristic: they are inherent features of programming languages or libraries. However, it took a considerable amount of time for them to be recognized as attack vectors and actual vulnerabilities. The existence of these vulnerabilities, previously unknown until their public disclosure, resulted in a substantial and previously unidentified attack surface for malicious actors. This discovery had…
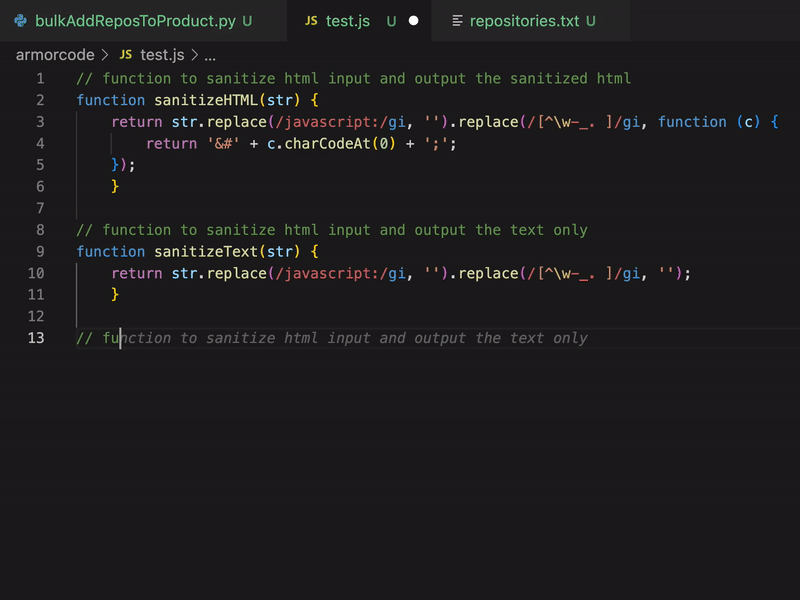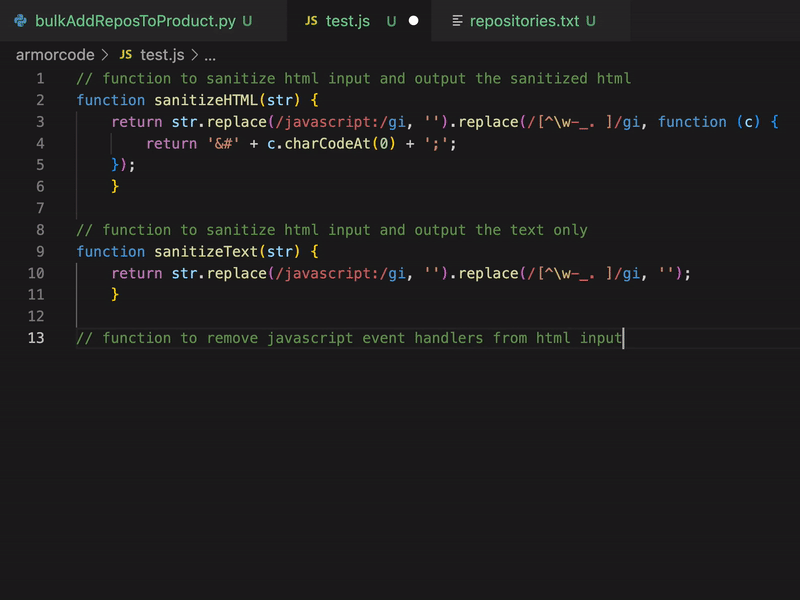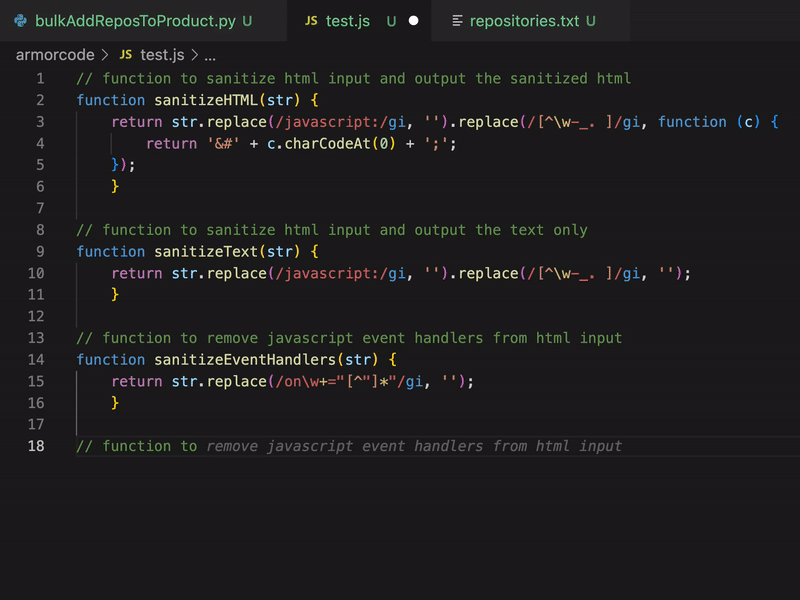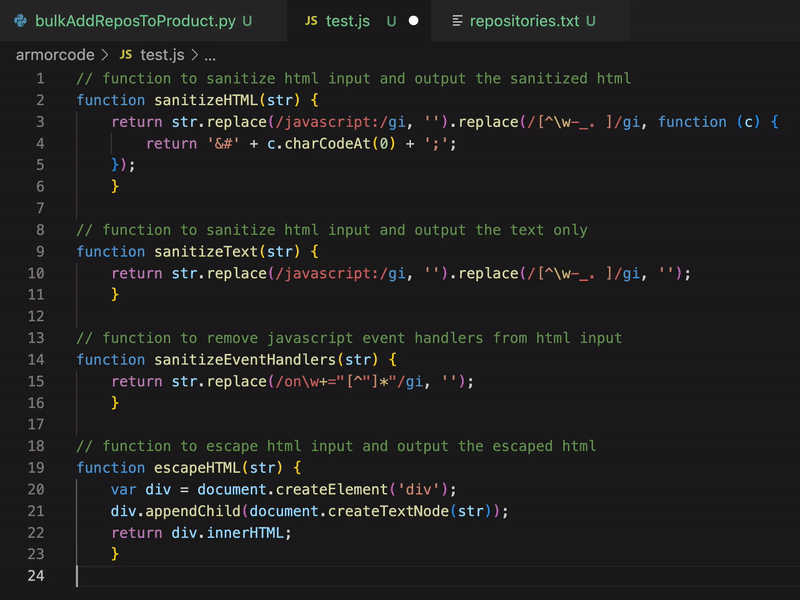
Leave a CommentToday I developed a python tool to automate some processes in our vulnerability management. For this task I decided to use GitHub Copilot. Mostly by using code comments (#, //) Copilot wrote the code for me, so I did not have to care much about syntax or function names, which I keep forgetting when I am not coding in Python…
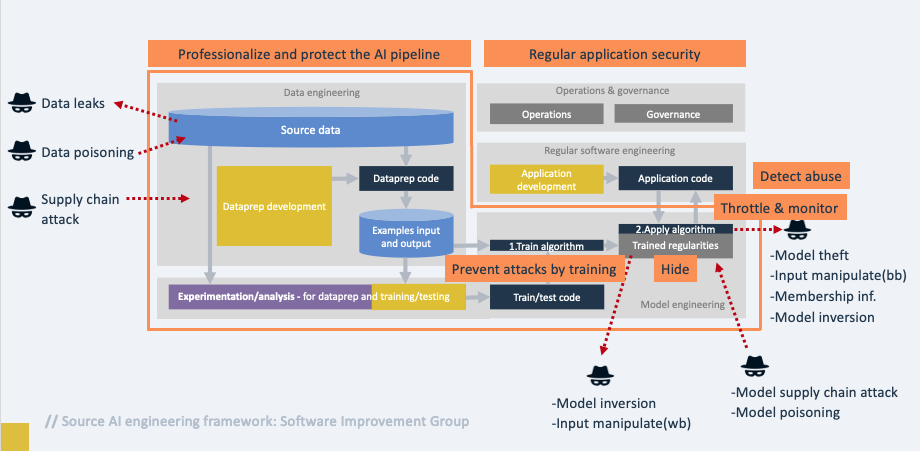
Leave a CommentIn today’s digital age, data has become a valuable asset for organizations, and it is collected, processed, and stored at an unprecedented rate. This data contains sensitive personal information that should be kept private, and if not handled with care, can cause severe consequences for individuals and organizations. As a result, privacy engineering has emerged as a crucial discipline that…
Leave a CommentLast month I attended the OWASP Global AppSec conference in San Francisco. The OWASP conference focuses exclusively on application security, and that’s what I liked about it. The people I met there have the same job description as me: we support software development teams in securing the software development lifecycle and we help to deliver secure products for our customers.…
Leave a CommentI just finished my talk at Ekoparty Security Conference Maintrack. It’s day 2 of three and the conference is just a blast. It is such a great selection of presentations and I am looking forward to the new connections I’ve made! Ya está disponible la charla de @javanrasokat: "A race against time" ▶️ https://t.co/dI6OoMwleO#MainTrackTalk #EKO2022 pic.twitter.com/GjmTqrWda2 — Ekoparty | Hacking…
Leave a CommentMit großer Freude durfte ich vergangenen Samstag Prof. Dr. Katja Wengler bei der Mastervorlesung “Software Quality Engineering” am DHBW Center for Advanced Studies (CAS) unterstützten. Das Modul “Software Quality Engineering” beschäftigt sich mit der Analyse von Softwaresystemen und deren Optimierung. Was ist Softwarequalität, wie kann Softwarequalität bewertet oder verbessert werden? Je nach Vorkenntnissen der Teilnehmer werden Themen wie Refactoring, Clean…
Leave a CommentI am already very excited that I will be giving a talk at Ekoparty security conference 2022 in Buenos Aires. #Eko2022 My talk outline: https://ekoparty.org/en_US/eko2022/main-track-talks-a-race-against-time-javan-rasokat Get your tickets here: https://ekoparty.org (free) #GlobalAppSecSanFran I am also looking forward to be part of the OWASP Global AppSec in San Francisco. My talk is on the last day of the conference. Check out…
Leave a CommentI was very pleased to give my presentation on race condition vulnerabilities in web applications at this year’s HITB conference in Singapore. The talks with the participants, the other presentations, the organisation, everything was very well done and I was able to exchange ideas with the security community in Singapore and internationally.The people, the city and the food are amazing.Many…
Leave a Comment