Two months ago I found a security issue in the Firefox integrated Password Manager and reported it. It was so obvious that I was really surprised. Of course, I was not the first to find this vulnerability. After I reported it, I was informed that it was known and that a bugfix for Firefox 73 was already available in beta. Ok, my mistake! The bug was also checked and noted as resolved by the person who reported it (see bug #1584126)
Since I had already looked deeper into the source code of the Firefox password manager at that time, I already knew that it was not really fixed. Instead, a fast beauty correction was made. Apparently also to slow down the amount of incoming bug reports, which also shows what security mechanism the bughunters would expect here.
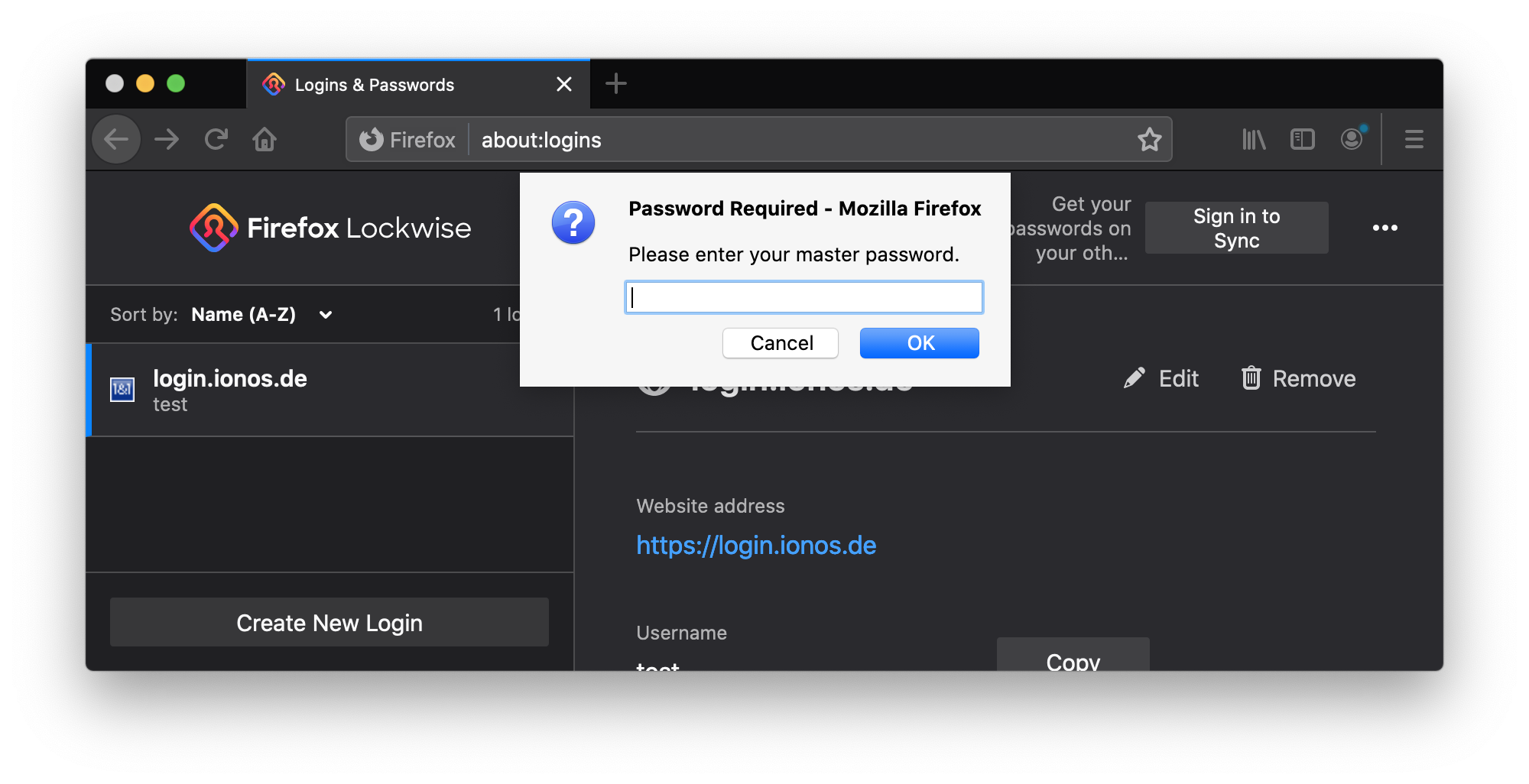
So I quickly delivered a bypass for this bugfix. It is still possible to bypass the Firefox master password. If a browser session has been opened once and the user has entered the master password once, all passwords can be read out by a visitor, even if the master password protection has been activated. The master password prompt can be easily bypassed, as the following video shows:
I’ve used the following attack vector, but any other is possible:
window.addEventListener("AboutLoginsLoginSelected", event => {
console.log(event);
alert(event.detail.username + ':' + event.detail.password);
});The bug has not been fixed in Firefox 73.0.1 so far. It could be implemented quite simply, as also suggested. Instead, I got the impression that it was a clear decision not to offer a fully functional security measure. I got the reference to this comment as a reason.
I think that speaks to the disagreement that almost the exact vulnerability in the past was given the rating Moderate and an Advisory was issued. I’m surprised that exactly the same scenario already occurred in the old Password Manager (before Firefox 70) and that there was CVE-2019-11733 for it. If you read the CVE description the attack scenario is nearly the same:
When a master password is set, it is required to be entered again before stored passwords can be accessed in the ‘Saved Logins’ dialog. It was found that locally stored passwords can be copied to the clipboard thorough the ‘copy password’ context menu item without re-entering the master password if the master password had been previously entered in the same session, allowing for potential theft of stored passwords.
Source: https://www.mozilla.org/en-US/security/advisories/mfsa2019-24/#CVE-2019-11733
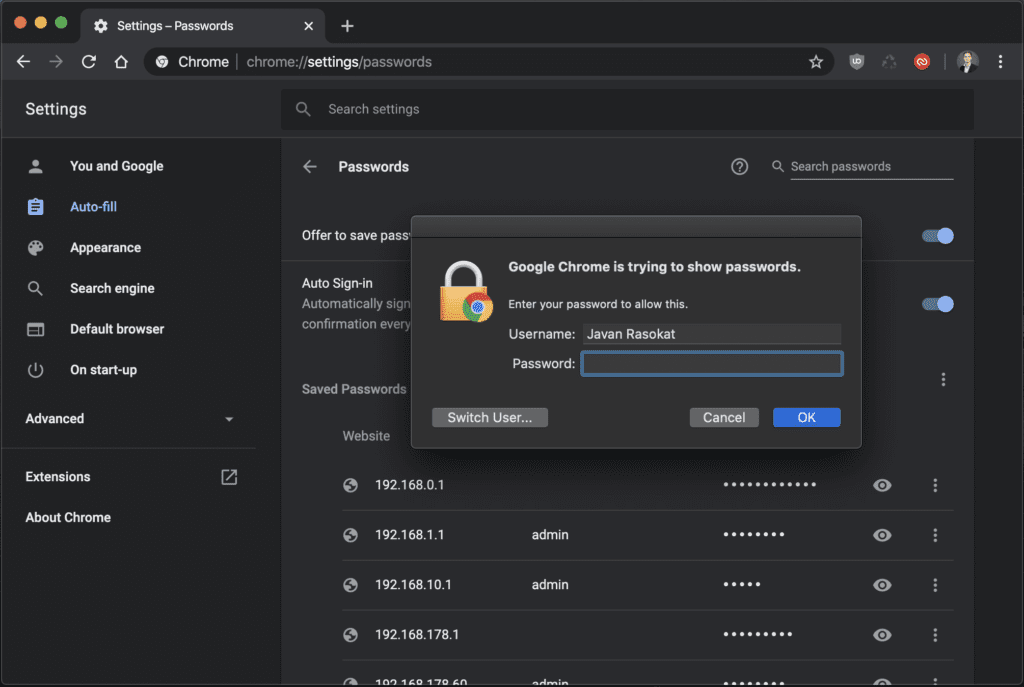
As I also said in my bug report, I find it ridiculous to refer to telemetry data that only a minority uses a master password. After all, we are talking about a now mature password manager in the browser, where my cross-device data is stored. Here you should clarify the changes that came with Lockwise into Firefox 70, or implement a solution as found in the Chrome browser. It is not recognizable for the user that the master password prompt actually only gives the appearance of a security check.
With Firefox Lockwise came the first really comfortable password manager that offers free cloud synchronization across all devices. Even the default password manager Keychain can be exchanged with Lockwise on the iPhone. This way all my passwords are (now unfortunately) stored in the Firefox browser on my laptop. On the iPhone, every access to the password list is still protected with a fingerprint or a PIN. But not so on the browser…
As a user you close your password manager like KeePass after you have copied your password. You don’t leave it unattended. Now after knowing that the Firefox master password prompt can be easily bypassed I would like to recommend to always close Firefox after usage or use the logout function hidden in the menu.
Maybe we should take a look at the Chrome, for example, which has found a working solution here. This password prompt can’t be bypassed.